The One Thing You Should Know
For Cybersecurity
If there’s one thing you should know for starting a career in Cyber Security…
It’s NMAP, Why? IT’S FUN!
Fun aside, dig a little deeper and this basic port scanning tool will teach you so much about the fundamentals of computer science and networking in general.
What is NMAP?
NMAP is one of the first “Security” tools I ever used and chances are it might be yours.
It’s pretty simple to start with, but the value it provides is huge. So what exactly is it? Nmap (Network Mapper) is a free and open-source network scanning tool used to discover hosts (other servers, PCs, devices basically) and services (what’s running on them) on a computer network - It was designed for quickly scanning large networks, but it also performs well on single hosts. It helps in network inventory and monitoring host or service up-time.
Core Knowledge
Okay, so we sort of understand what it is but to make things clearer let's take a look at why we would use it in 3 short sweet points.
Network Discovery: Identifies devices on a network.
Service Discovery: Finds open ports and running services.
Network Inventory: Maps the network structure.
Building on that let's look at the output we can expect from NMAP:
The output generated by NMAP includes a list of scanned targets and the IP address, along with additional details based on the chosen options.
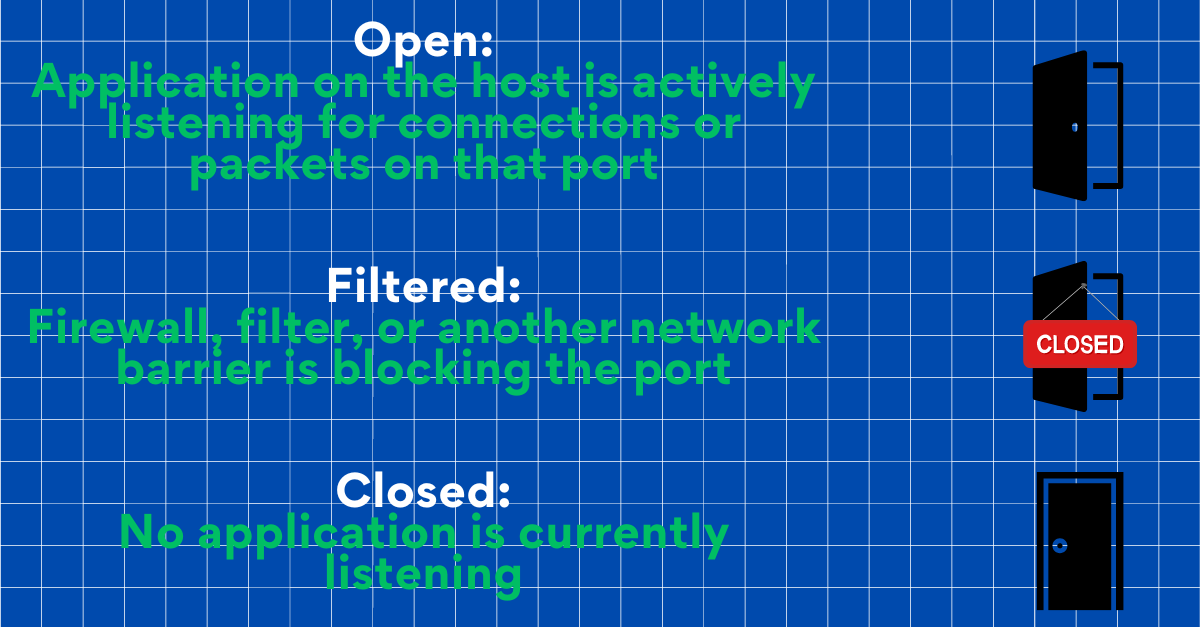
NMAP really comes alive when we have selected a Host to scan. This scan will return the port number and protocol, service name, and state. The state and the output generated by NMAP include a list of scanned targets along with additional details based on the chosen options. A crucial part of this output is the "interesting ports table," which provides the port number and protocol, service name, and state. The state can be open, filtered or closed.
We may also see unfiltered, this is where NMAP can’t tell the state of the port.
Getting Started
Before we get hands-on, let’s take the time to understand how NMAP actually works. It’s really important, especially with tools like this that you understand what’s going on under the hood here. It’s what’s going to make you stand out and ultimately make you a better engineer.
NMAP goes through Four stages: Discovery, Port Scanning, Service Detection and OS Detection:
Discovery:
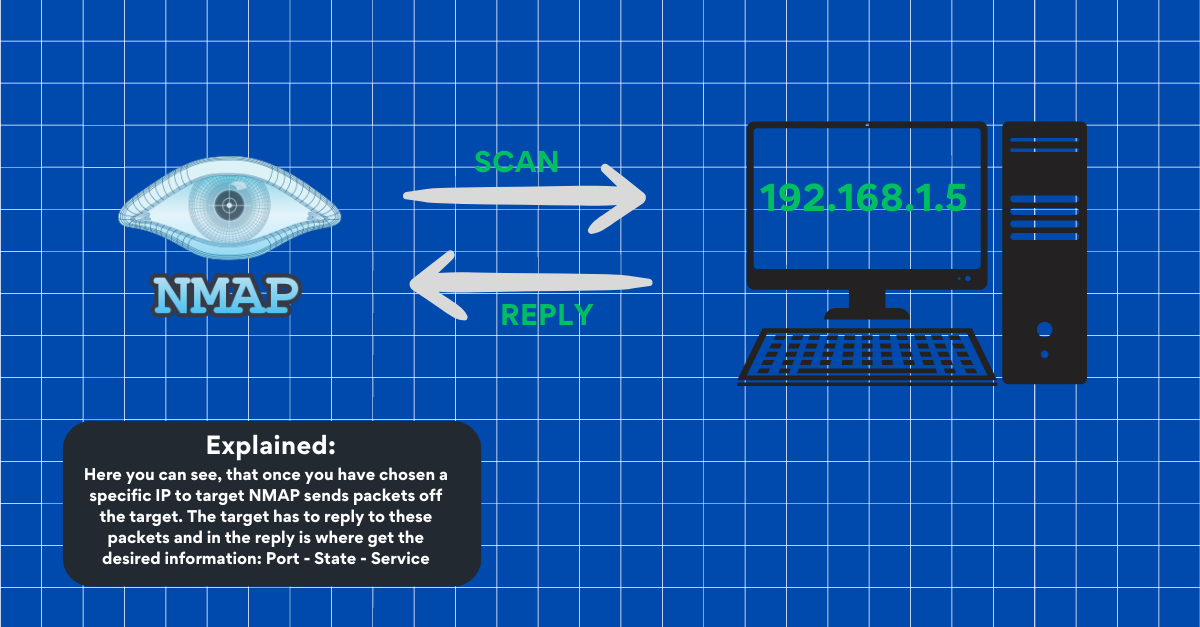
Packet Sent: Nmap sends a "ping" using either ICMP (like an echo request) or a TCP/UDP packet to see if devices are online.
Reply: If the device is online, it responds with a "pong" (ICMP echo reply) or a TCP/UDP response.
Port Scanning:
Packet Sent: Nmap sends a TCP SYN packet (like knocking on a door) to different ports (numbers assigned to specific services) or sends a UDP packet.
Reply: This is where we will see a list of our service and ports. Remember - Open port, closed port and filtered port:Service Detection:
Packet Sent: Nmap sends specific packets that mimic requests for different services (like asking for a webpage).
Reply: The service responds with information about itself (like saying "I'm a web server running version 1.2").OS Detection:
Packet Sent: Nmap sends various TCP and UDP packets with slight modifications.
Reply: Different operating systems respond in unique ways, and Nmap uses these differences to guess the operating system.
So, NMAP sends packets and looks at how devices reply to figure out which devices are online, which ports are open, what services are running, and what operating systems are in use.
Project time!
You’ll have to grab a copy of TechOneTwenty for this 😉
Thank you for reading: Keep it secure, keep it light-hearted!
WJPearce - CyberBrew
Enjoyed this? Why not check out my other reads…
The Top Five Kali Linux Tools 🐉
Cyber Careers: The Guide You Need 💼